Protecting your environment is a complex and critical task. At every turn, it seems, attackers can penetrate your network and abuse its protocols through network redirection attacks, also known as “poisoning attacks.” Some protocols are particularly vulnerable to abuse. Learning what attackers might be planning and what antidotes are available can help mitigate damage that poisoning attacks might inflict.
What attackers are up to
It’s well established that attackers are trying to break into your network, but what remains unclear is what they do once they get there. After attackers gain network access and establish the ability to communicate with and route traffic to other devices on the network, they often continue the attack by manipulating or redirecting whatever traffic they can see. Through poisoning attacks, attackers can use the network protocols that transmit information to funnel more sensitive traffic from intended systems to another target or even back to the attacker-owned device.
An earlier post explored NetBIOS and LLMNR– two commonly exploited network protocols used for name resolution – and how attackers use them to redirect authentication traffic and steal credentials. If you’ve a) read that post, b) ever had a pentest, or c) followed a hardening guide, then hopefully you’ve followed the advice given, disabled those protocols, and maybe even blocked the ports the protocols use on host firewalls.
So, if these attack vectors are no longer effective, what else might attackers try to do in your environment?
Most likely, hungry attackers will try to translate that network access to authenticated access. Even if a peek of the local network traffic on Wireshark doesn’t reveal NetBIOS or LLMNR broadcasts, attackers still have a couple of tricks up their sleeves. Those tricks involve other poisoning techniques, including abusing three protocols: multicast domain name system (mDNS), internet protocol version 6 (IPv6), and Address Resolution Protocol (ARP).
Let’s dive in and explore what these protocols are, how they are vulnerable, and what antidotes are available to mitigate damage.
mDNS
One protocol vulnerable to poisoning attacks is mDNS. The DNS translates human-readable names (such as “website.com”) to their associated network locations, represented by an IP address (“x.x.x.x”). A DNS lookup transaction is usually unicast, meaning a single computer will ask a single server to translate a name to an IP address.
Instead of asking a single server, mDNS, a DNS-related protocol, sends out a packet to other hosts around it to essentially crowdsource the answer to the query, “Where is this thing located?” In addition, mDNS is used in conjunction with DNS service discovery, which helps discover lists of available services via DNS. These features are helpful on home networks where local DNS servers don’t exist and computers need to find other local resources such as printers. One serial user of the mDNS protocol is Apple’s Bonjour service, meaning that mDNS can be observed in heavy use on networks containing MacOS and iOS devices.
Much like when attackers set out to abuse NetBIOS and LLMNR, mDNS can be abused via an attacker answering an mDNS request and impersonating a legitimate resource or computer on a network. Attackers can even use the same tool, the notorious “Responder,” as published by Trustwave’s SpiderLabs in 2013. The result is that the attacker can cause a device to send sensitive information directly to the attacker’s machine, whether that be a print job for a document containing personal information or worse: a user’s credentials.
IPv6
Another protocol susceptible to abuse is IPv6. IPv6 is the wave of the future – or at least it was supposed to be.
First, a quick math lesson: If IPv4 addresses are represented by four octets (“1.2.3.4”) and each quadrant can hold a value between 0 and 255 (~2^8), that means the total possible number of IPv4 addresses is around 4.2 billion. There are almost 8 billion people on Earth, so if a quarter of us have at least two devices communicating on the internet and each one of those internet devices needs IP addresses so the traffic knows where to go, something doesn’t add up: How can we possibly have enough IP addresses?
Next, an even quicker history lesson: Around 1998, the Internet Engineering Task Force recognized this problem and came up with a new addressing scheme called IPv6 that could hold 2^128 (340 trillion trillion) addresses, which is more addresses than there are grains of sand on Earth. This standard would take some time to implement, as old devices would have compatibility issues.
In the meantime, some clever networking gurus implemented a technology called network address translation and reserved private addresses to solve that problem. (To illustrate, consider how each apartment building in a city can use the same apartment numbers but have different street addresses.) The takeaway here is that, moving forward, all networked devices were “future-proofed” for the impending switch to IPv6.
What does the switch mean for attackers? Significantly, when networked devices were future-proofed, they were configured by default to accept IPv6 addresses over IPv4 addresses so that when the switch was finally made, the transition could be seamless.
However, because most internal networks still assign IPv4 addresses, attackers can pose as an IPv6 router, take priority over a network’s actual routers, and assign addresses as they please via rogue router advertisements. This method is referred to as a stateless address auto configuration (SLAAC) attack. Its sleeker cousin, which abuses DNS only for select targets and causes fewer availability issues, is called a man-in-the-middle-v6 (MitM6) attack, named after the tool used to execute the attack.
Via the MitM6 attack, attackers can fire up the MitM6 tool to produce rogue router advertisements, declare themselves the authoritative DNS server, and trick devices into sending authentication traffic and other sensitive information to an attacker-controlled machine. The information can then be either captured or relayed to another machine on which the authentication can be further abused to perform more malicious actions.
ARP
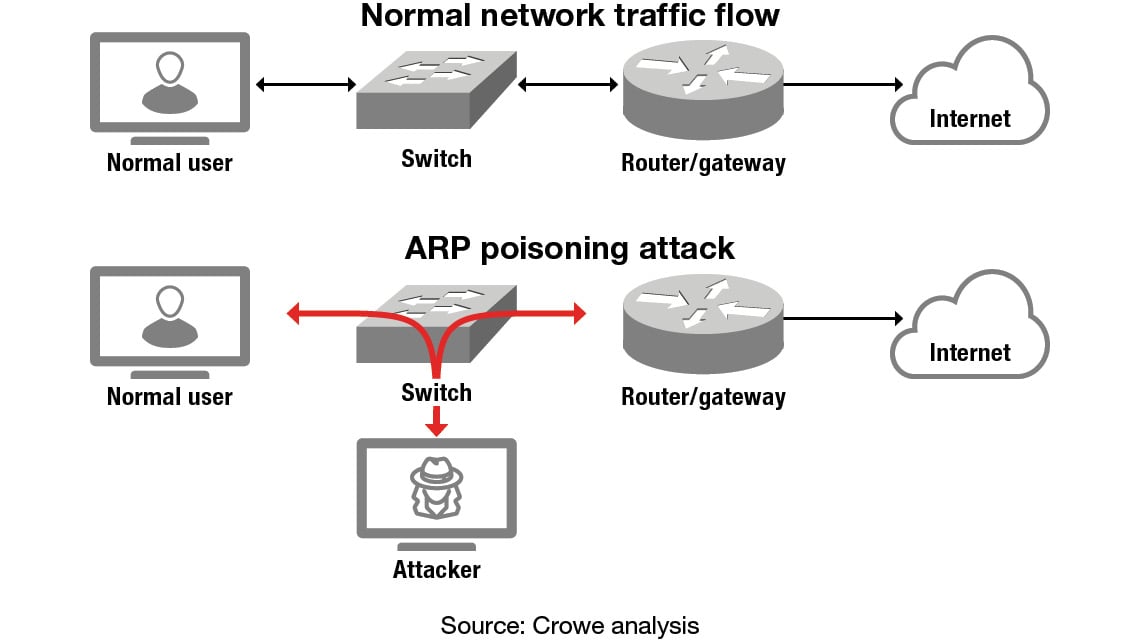
A third protocol that is targeted by poisoning attacks is ARP, an oldie but a goodie. ARP is a bit more primitive than the more sophisticated protocols mDNS and IPv6, but that’s understandable since it’s been around since 1982 and operates a little lower on the food chain from a network layer perspective.
ARP is paramount on modern networks, however, because it’s the protocol that helps link devices’ physical addresses (MAC addresses) to IP addresses so that devices can route communications with each other and the internet.
The abuse of ARP – known as ARP poisoning, spoofing, and flooding – has been in use for more than two decades and as such has been well documented. In an ARP poisoning attack, attackers flood a network switch with so many entries for device-to-address pairings that the attackers eventually overwrite the original entries and can assign addresses as they please. This method allows attackers to gain a man-in-the-middle position. From this position on the network, attackers can send and receive traffic intended for other devices and therefore become privy to all the information held within that traffic.
ARP poisoning attack diagram
The antidotes
With these three protocols and their respective abuses, attackers manipulate how the protocols operate on a network in order to divulge sensitive or valuable information. Likewise, many of the fixes to prevent this manipulation also live at the network level.
For mDNS, the service can be disabled on all hosts that are using it, namely MacOS devices running the Bonjour service. Alternatively, both network and local device firewalls can be updated to either block connections on UDP port 5353 altogether or allow access only to trusted devices.
For IPv6, it’s a use-it-or-lose-it situation. Administrators should either configure routers to operate via IPv6 and use IPv6 addressing, or dynamic host configuration protocol version 6 (DHCPv6) and IPv6 router advertisements should be blocked and IPv6 disabled on all hosts. Alternatively, if there’s a use case for IPv6 in Microsoft Windows™ environments, a group policy can be configured to prefer IPv4 over IPv6 to prevent an attack.
For ARP, networking devices such as switches should be configured with DHCP snooping as well as dynamic ARP inspection (DAI). DHCP snooping and DAI are security mechanisms that help maintain a record of which devices are bound to which IP addresses and validate that ARP traffic is not being forged by malicious hosts, respectively.
Staying poison-free
The root of the problem of poisoning attacks is that these protocols are either enabled by default or are completely necessary for normal network usage. Attackers have found ways to abuse the implicit trust of these network protocols and make them a stepping stone in an attack on your environment.
To stop attackers in their tracks, organizations must enable security controls in their environments by hardening not just endpoints but networking devices as well. More information on securing networking devices is available through the Cybersecurity and Infrastructure Security Agency (CISA), the Center for Internet Security (CIS), and Cisco.
Taking action against poisoning attacks today can help your organization prevent damage tomorrow. Outsmart the attackers and stay poison-free by hardening your environment.
Microsoft and Microsoft Windows are either registered trademarks or trademarks of Microsoft Corp. in the United States and/or other countries.
